Smart contracts power decentralized apps (DApps) on blockchains like Ethereum, handling billions in assets. But a single coding mistake can lead to hacks or loss of funds. Auditing a smart contract ensures it’s secure, reliable, and bug-free. This beginner-friendly guide walks you through the process of auditing a smart contract, using simple tools and techniques. Whether you’re a developer or curious about blockchain security, let’s dive in!

Why Audit Smart Contracts?
Smart contracts are immutable once deployed, meaning bugs can’t be fixed easily. A flaw could allow hackers to steal funds, as seen in incidents like the 2016 DAO hack. Auditing helps:
- Prevent Hacks: Identify vulnerabilities before deployment.
- Build Trust: Assure users your DApp is secure.
- Save Costs: Avoid costly exploits or emergency fixes.
For developers, auditing is a critical skill to create safe DApps for DeFi, NFTs, or gaming.
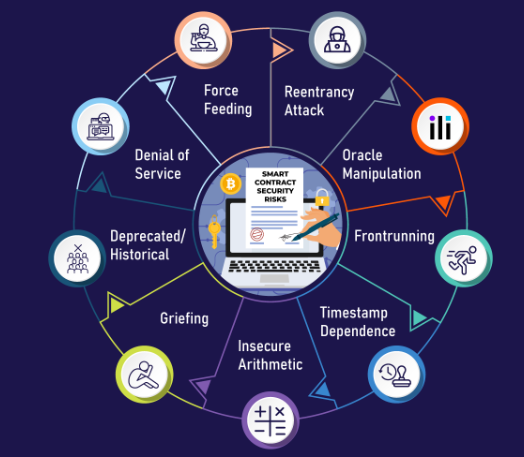
Common Smart Contract Vulnerabilities
Before auditing, let’s understand the most common issues to look for:
- Reentrancy: A contract calls another before finishing its operation, allowing attackers to drain funds.
- Integer Overflow/Underflow: Math errors due to improper variable handling, leading to unexpected behavior.
- Access Control: Missing checks that allow unauthorized users to call sensitive functions.
- Gas Limit Issues: Loops or operations that consume excessive gas, causing transactions to fail.
Knowing these helps you focus your audit on high-risk areas.
Tools for Auditing Smart Contracts
Several tools make auditing easier by automatically detecting issues or helping manual reviews. Here are the most popular:
- Slither: A static analysis tool for Solidity. Install via github.com/crytic/slither.
- MythX: A cloud-based security scanner for Ethereum contracts. Learn more at mythx.io.
- Hardhat: For testing and debugging contracts. Install from hardhat.org.
- Remix: A web-based IDE with built-in static analysis for Solidity. Access at remix.ethereum.org.
We’ll use these tools in our auditing process.
Step-by-Step: Auditing a Smart Contract
Let’s audit a simple Solidity smart contract to identify vulnerabilities. We’ll use a sample contract, analyze it manually, and run automated tools for a thorough check.
Step 1: Understand the Contract
Start by reviewing the contract’s purpose and logic. Here’s a sample contract (contracts/VulnerableBank.sol) with potential issues:
// SPDX-License-Identifier: MIT
pragma solidity ^0.8.0;
contract VulnerableBank {
mapping(address => uint256) public balances;
function deposit() external payable {
balances[msg.sender] += msg.value;
}
function withdraw(uint256 amount) external {
require(balances[msg.sender] >= amount, "Insufficient balance");
(bool success, ) = msg.sender.call{value: amount}("");
require(success, "Transfer failed");
balances[msg.sender] -= amount;
}
function getBalance() external view returns (uint256) {
return balances[msg.sender];
}
}
This contract allows users to deposit and withdraw ETH but may have vulnerabilities. Let’s audit it.
Step 2: Manual Code Review
Read the code line-by-line to spot issues. Look for:
- Reentrancy: In
withdraw, the external call (msg.sender.call) happens before updatingbalances. An attacker could re-enter the function, withdrawing multiple times before their balance is updated. - Access Control: No restrictions on who can call
depositorwithdraw, but this seems intentional for a public bank. - Gas Issues: No unbounded loops, so gas usage appears safe.
Fix Reentrancy: Update withdraw to use the checks-effects-interactions pattern:
function withdraw(uint256 amount) external {
require(balances[msg.sender] >= amount, "Insufficient balance");
balances[msg.sender] -= amount; // Update state first
(bool success, ) = msg.sender.call{value: amount}("");
require(success, "Transfer failed");
}
Manual reviews catch logical errors that tools might miss.

Step 3: Run Automated Tools
Use Slither to analyze the contract. Install Slither:
pip install slither-analyzer
Run Slither on the contract:
slither contracts/VulnerableBank.sol
Slither may flag the reentrancy issue in the original withdraw function and suggest other optimizations, like using OpenZeppelin’s ReentrancyGuard. Update the contract to include it:
// SPDX-License-Identifier: MIT
pragma solidity ^0.8.0;
import "@openzeppelin/contracts/security/ReentrancyGuard.sol";
contract VulnerableBank is ReentrancyGuard {
mapping(address => uint256) public balances;
function deposit() external payable {
balances[msg.sender] += msg.value;
}
function withdraw(uint256 amount) external nonReentrant {
require(balances[msg.sender] >= amount, "Insufficient balance");
balances[msg.sender] -= amount;
(bool success, ) = msg.sender.call{value: amount}("");
require(success, "Transfer failed");
}
function getBalance() external view returns (uint256) {
return balances[msg.sender];
}
}
Re-run Slither to confirm the fix.
Step 4: Write Unit Tests
Create tests to simulate attacks and ensure the contract behaves correctly. Add a test file in test/BankTest.js:
const { expect } = require("chai");
const { ethers } = require("hardhat");
describe("VulnerableBank", function () {
let bank, owner, user1;
beforeEach(async function () {
[owner, user1] = await ethers.getSigners();
const VulnerableBank = await ethers.getContractFactory("VulnerableBank");
bank = await VulnerableBank.deploy();
await bank.deployed();
});
it("should allow deposits and withdrawals", async function () {
await bank.connect(user1).deposit({ value: ethers.parseEther("1") });
expect(await bank.getBalance({ from: user1.address })).to.equal(ethers.parseEther("1"));
await bank.connect(user1).withdraw(ethers.parseEther("1"));
expect(await bank.getBalance({ from: user1.address })).to.equal(0);
});
it("should prevent reentrancy attacks", async function () {
const Attack = await ethers.getContractFactory("Attack");
const attack = await Attack.deploy(bank.address);
await attack.deployed();
await expect(attack.attack({ value: ethers.parseEther("1") })).to.be.reverted;
});
});
Create an attack contract (contracts/Attack.sol) to test reentrancy:
// SPDX-License-Identifier: MIT
pragma solidity ^0.8.0;
contract Attack {
VulnerableBank public bank;
constructor(address _bank) {
bank = VulnerableBank(_bank);
}
function attack() external payable {
bank.deposit{value: msg.value}();
bank.withdraw(msg.value);
}
receive() external payable {
if (address(bank).balance >= msg.value) {
bank.withdraw(msg.value);
}
}
}
Run tests with npx hardhat test. The reentrancy guard should prevent the attack.
Step 5: Deploy and Test on Testnet
Deploy the fixed contract to Sepolia. Update hardhat.config.js with your API key (from Infura or Alchemy):
require("@nomicfoundation/hardhat-toolbox");
module.exports = {
solidity: "0.8.0",
networks: {
sepolia: {
url: "https://sepolia.infura.io/v3/YOUR_API_KEY",
accounts: ["YOUR_PRIVATE_KEY"]
}
}
};
Create a deployment script in scripts/deploy.js:
const hre = require("hardhat");
async function main() {
const VulnerableBank = await hre.ethers.getContractFactory("VulnerableBank");
const bank = await VulnerableBank.deploy();
await bank.deployed();
console.log("VulnerableBank deployed to:", bank.address);
}
main().catch((error) => {
console.error(error);
process.exitCode = 1);
});
Deploy with npx hardhat run scripts/deploy.js --network sepolia. Test the contract using MetaMask and test ETH from sepoliafaucet.com.
Benefits of Auditing Smart Contracts
Auditing offers significant advantages:
- Enhanced Security: Protects user funds and DApp reputation.
- User Confidence: Audited contracts attract more users and investors.
- Cost Savings: Prevents expensive hacks or redeployments.
Auditing is essential for any serious blockchain project.
Challenges of Smart Contract Auditing
Auditing isn’t without hurdles:
- Complexity: Requires deep knowledge of Solidity and blockchain security.
- Time-Intensive: Thorough audits can take days or weeks.
- False Positives: Automated tools may flag non-issues, requiring manual verification.
Combine manual reviews with tools and consider hiring professional auditors for critical projects.
Tips for Developers Auditing Smart Contracts
To audit effectively:
- Follow Best Practices: Use OpenZeppelin’s secure contracts and patterns like checks-effects-interactions.
- Use Multiple Tools: Combine Slither, MythX, and Remix for comprehensive analysis.
- Write Extensive Tests: Cover edge cases and attack scenarios with Hardhat or Truffle.
- Learn from Audits: Study reports from ConsenSys Diligence to understand common issues.
These practices ensure your audits are thorough and reliable.
Resources for Learning More
Deepen your auditing skills with these resources:
- Ethereum Docs: Smart contract security at ethereum.org.
- OpenZeppelin: Secure contract templates at docs.openzeppelin.com.
- Blockchain Communities: Join discussions on Ethereum Stack Exchange or security forums.
Stay curious to master smart contract security.
Conclusion
Auditing smart contracts is a critical step to ensure blockchain DApps are secure and trustworthy. By combining manual reviews, automated tools like Slither, and thorough testing, you can identify and fix vulnerabilities like reentrancy. Start auditing your contracts today, and share your security tips in the comments below!






















